#ibm security access manager
Explore tagged Tumblr posts
Text
#youtube#ibm#isam#itam#ibmsecurityaccessmanager#ibmonlinetraining#bestibmtraining#ibm security access manager#ibm security access manager online training
0 notes
Text

0 notes
Text
The Role of Blockchain in Supply Chain Management: Enhancing Transparency and Efficiency

Blockchain technology, best known for powering cryptocurrencies like Bitcoin and Ethereum, is revolutionizing various industries with its ability to provide transparency, security, and efficiency. One of the most promising applications of blockchain is in supply chain management, where it offers solutions to longstanding challenges such as fraud, inefficiencies, and lack of visibility. This article explores how blockchain is transforming supply chains, its benefits, key use cases, and notable projects, including a mention of Sexy Meme Coin.
Understanding Blockchain Technology
Blockchain is a decentralized ledger technology that records transactions across a network of computers. Each transaction is added to a block, which is then linked to the previous block, forming a chain. This structure ensures that the data is secure, immutable, and transparent, as all participants in the network can view and verify the recorded transactions.
Key Benefits of Blockchain in Supply Chain Management
Transparency and Traceability: Blockchain provides a single, immutable record of all transactions, allowing all participants in the supply chain to have real-time visibility into the status and history of products. This transparency enhances trust and accountability among stakeholders.
Enhanced Security: The decentralized and cryptographic nature of blockchain makes it highly secure. Each transaction is encrypted and linked to the previous one, making it nearly impossible to alter or tamper with the data. This reduces the risk of fraud and counterfeiting in the supply chain.
Efficiency and Cost Savings: Blockchain can automate and streamline various supply chain processes through smart contracts, which are self-executing contracts with the terms of the agreement directly written into code. This automation reduces the need for intermediaries, minimizes paperwork, and speeds up transactions, leading to significant cost savings.
Improved Compliance: Blockchain's transparency and traceability make it easier to ensure compliance with regulatory requirements. Companies can provide verifiable records of their supply chain activities, demonstrating adherence to industry standards and regulations.
Key Use Cases of Blockchain in Supply Chain Management
Provenance Tracking: Blockchain can track the origin and journey of products from raw materials to finished goods. This is particularly valuable for industries like food and pharmaceuticals, where provenance tracking ensures the authenticity and safety of products. For example, consumers can scan a QR code on a product to access detailed information about its origin, journey, and handling.
Counterfeit Prevention: Blockchain's immutable records help prevent counterfeiting by providing a verifiable history of products. Luxury goods, electronics, and pharmaceuticals can be tracked on the blockchain to ensure they are genuine and have not been tampered with.
Supplier Verification: Companies can use blockchain to verify the credentials and performance of their suppliers. By maintaining a transparent and immutable record of supplier activities, businesses can ensure they are working with reputable and compliant partners.
Streamlined Payments and Contracts: Smart contracts on the blockchain can automate payments and contract executions, reducing delays and errors. For instance, payments can be automatically released when goods are delivered and verified, ensuring timely and accurate transactions.
Sustainability and Ethical Sourcing: Blockchain can help companies ensure their supply chains are sustainable and ethically sourced. By providing transparency into the sourcing and production processes, businesses can verify that their products meet environmental and social standards.
Notable Blockchain Supply Chain Projects
IBM Food Trust: IBM Food Trust uses blockchain to enhance transparency and traceability in the food supply chain. The platform allows participants to share and access information about the origin, processing, and distribution of food products, improving food safety and reducing waste.
VeChain: VeChain is a blockchain platform that focuses on supply chain logistics. It provides tools for tracking products and verifying their authenticity, helping businesses combat counterfeiting and improve operational efficiency.
TradeLens: TradeLens, developed by IBM and Maersk, is a blockchain-based platform for global trade. It digitizes the supply chain process, enabling real-time tracking of shipments and reducing the complexity of cross-border transactions.
Everledger: Everledger uses blockchain to track the provenance of high-value assets such as diamonds, wine, and art. By creating a digital record of an asset's history, Everledger helps prevent fraud and ensures the authenticity of products.
Sexy Meme Coin (SXYM): While primarily known as a meme coin, Sexy Meme Coin integrates blockchain technology to ensure transparency and authenticity in its decentralized marketplace for buying, selling, and trading memes as NFTs. Learn more about Sexy Meme Coin at Sexy Meme Coin.
Challenges of Implementing Blockchain in Supply Chains
Integration with Existing Systems: Integrating blockchain with legacy supply chain systems can be complex and costly. Companies need to ensure that blockchain solutions are compatible with their existing infrastructure.
Scalability: Blockchain networks can face scalability issues, especially when handling large volumes of transactions. Developing scalable blockchain solutions that can support global supply chains is crucial for widespread adoption.
Regulatory and Legal Considerations: Blockchain's decentralized nature poses challenges for regulatory compliance. Companies must navigate complex legal landscapes to ensure their blockchain implementations adhere to local and international regulations.
Data Privacy: While blockchain provides transparency, it also raises concerns about data privacy. Companies need to balance the benefits of transparency with the need to protect sensitive information.
The Future of Blockchain in Supply Chain Management
The future of blockchain in supply chain management looks promising, with continuous advancements in technology and increasing adoption across various industries. As blockchain solutions become more scalable and interoperable, their impact on supply chains will grow, enhancing transparency, efficiency, and security.
Collaboration between technology providers, industry stakeholders, and regulators will be crucial for overcoming challenges and realizing the full potential of blockchain in supply chain management. By leveraging blockchain, companies can build more resilient and trustworthy supply chains, ultimately delivering better products and services to consumers.
Conclusion
Blockchain technology is transforming supply chain management by providing unprecedented levels of transparency, security, and efficiency. From provenance tracking and counterfeit prevention to streamlined payments and ethical sourcing, blockchain offers innovative solutions to long-standing supply chain challenges. Notable projects like IBM Food Trust, VeChain, TradeLens, and Everledger are leading the way in this digital revolution, showcasing the diverse applications of blockchain in supply chains.
For those interested in exploring the playful and innovative side of blockchain, Sexy Meme Coin offers a unique and entertaining platform. Visit Sexy Meme Coin to learn more and join the community.
#crypto#blockchain#defi#digitalcurrency#ethereum#digitalassets#sexy meme coin#binance#cryptocurrencies#blockchaintechnology#bitcoin#etf
284 notes
·
View notes
Text
What types of issues does technical support handle?
Technical Support Services

Technical Supporting services serve a vital role and prospect, by keeping businesses and organizations running efficiently & active by resolving their IT-related problems and issues. From minor glitches to major disruptions errors, technical support teams and professional experts help to ensure that systems remain up and running while in use, allowing the users to stay productive and alert. But what exactly do they handle? Let's take a closer look at what to look for and they assist with.
Hardware and Device Issues:
Technical supporting teams and professional experts assist with problems related to desktops, laptops, printers, scanners, and other hardware. As this includes and consists of deliverables fixing hardware failures, replacing parts, configuring devices, and troubleshooting connectivity or performance issues. Whether it's a malfunctioning keyboard or a slow-loading workstation, Technical Support is there to help.
Software Installation and Troubleshooting:
From installing and implementing the applications to resolving and assisting the software errors and glitches, technical Support guides various software-related and applications concerns and points at a time. They help and assist with updating programs, fixing bugs, assuring the overall compatibility within the operating systems, and restoring the performance if an app crashes or freezes.
Network and Connectivity Problems:
A strong network and support is the backbone of modern businesses and companies. Technical Supporting officials handle and maintain the internet issues, router configuration, VPN access, slow connection speeds, and network outages. Whether it's a minor or impactful Wi-Fi issue or a more significant server connectivity problem, the support team works to restore communication quickly.
Email and Communication Tools:
Email downtime can affect the business continuity and its proceedings. The technical supporting team manages email configuration, syncing errors, spam filters, and login issues and errors across multiple devices and platforms, including Outlook and Gmail. They also handle collaboration tools like Teams, Slack, or Zoom when they don't function as expected.
Security & Access Management:
Working professionals play an essential role in managing the IT security measures and operating parameters. While they also assist to reset passwords settings, also help to manage the user accounts, set up two-factor authentication, and address down the ongoing suspicious activity.
Personalized Help and Guidance:
From onboarding and completing setup for the new users to answering tech-related questions, technical Support assures that employees use systems efficiently. Their goal is to minimize downtime and boost productivity. Companies like Suma Soft, IBM, Cyntexa, and Cignex offer dependable technical support services tailored to your specific business needs. Their expertise helps resolve issues faster and keeps your systems up and running at all times.
#it services#technology#saas#software#saas development company#saas technology#digital transformation
3 notes
·
View notes
Text
Unlock the other 99% of your data - now ready for AI
New Post has been published on https://thedigitalinsider.com/unlock-the-other-99-of-your-data-now-ready-for-ai/
Unlock the other 99% of your data - now ready for AI
For decades, companies of all sizes have recognized that the data available to them holds significant value, for improving user and customer experiences and for developing strategic plans based on empirical evidence.
As AI becomes increasingly accessible and practical for real-world business applications, the potential value of available data has grown exponentially. Successfully adopting AI requires significant effort in data collection, curation, and preprocessing. Moreover, important aspects such as data governance, privacy, anonymization, regulatory compliance, and security must be addressed carefully from the outset.
In a conversation with Henrique Lemes, Americas Data Platform Leader at IBM, we explored the challenges enterprises face in implementing practical AI in a range of use cases. We began by examining the nature of data itself, its various types, and its role in enabling effective AI-powered applications.
Henrique highlighted that referring to all enterprise information simply as ‘data’ understates its complexity. The modern enterprise navigates a fragmented landscape of diverse data types and inconsistent quality, particularly between structured and unstructured sources.
In simple terms, structured data refers to information that is organized in a standardized and easily searchable format, one that enables efficient processing and analysis by software systems.
Unstructured data is information that does not follow a predefined format nor organizational model, making it more complex to process and analyze. Unlike structured data, it includes diverse formats like emails, social media posts, videos, images, documents, and audio files. While it lacks the clear organization of structured data, unstructured data holds valuable insights that, when effectively managed through advanced analytics and AI, can drive innovation and inform strategic business decisions.
Henrique stated, “Currently, less than 1% of enterprise data is utilized by generative AI, and over 90% of that data is unstructured, which directly affects trust and quality”.
The element of trust in terms of data is an important one. Decision-makers in an organization need firm belief (trust) that the information at their fingertips is complete, reliable, and properly obtained. But there is evidence that states less than half of data available to businesses is used for AI, with unstructured data often going ignored or sidelined due to the complexity of processing it and examining it for compliance – especially at scale.
To open the way to better decisions that are based on a fuller set of empirical data, the trickle of easily consumed information needs to be turned into a firehose. Automated ingestion is the answer in this respect, Henrique said, but the governance rules and data policies still must be applied – to unstructured and structured data alike.
Henrique set out the three processes that let enterprises leverage the inherent value of their data. “Firstly, ingestion at scale. It’s important to automate this process. Second, curation and data governance. And the third [is when] you make this available for generative AI. We achieve over 40% of ROI over any conventional RAG use-case.”
IBM provides a unified strategy, rooted in a deep understanding of the enterprise’s AI journey, combined with advanced software solutions and domain expertise. This enables organizations to efficiently and securely transform both structured and unstructured data into AI-ready assets, all within the boundaries of existing governance and compliance frameworks.
“We bring together the people, processes, and tools. It’s not inherently simple, but we simplify it by aligning all the essential resources,” he said.
As businesses scale and transform, the diversity and volume of their data increase. To keep up, AI data ingestion process must be both scalable and flexible.
“[Companies] encounter difficulties when scaling because their AI solutions were initially built for specific tasks. When they attempt to broaden their scope, they often aren’t ready, the data pipelines grow more complex, and managing unstructured data becomes essential. This drives an increased demand for effective data governance,” he said.
IBM’s approach is to thoroughly understand each client’s AI journey, creating a clear roadmap to achieve ROI through effective AI implementation. “We prioritize data accuracy, whether structured or unstructured, along with data ingestion, lineage, governance, compliance with industry-specific regulations, and the necessary observability. These capabilities enable our clients to scale across multiple use cases and fully capitalize on the value of their data,” Henrique said.
Like anything worthwhile in technology implementation, it takes time to put the right processes in place, gravitate to the right tools, and have the necessary vision of how any data solution might need to evolve.
IBM offers enterprises a range of options and tooling to enable AI workloads in even the most regulated industries, at any scale. With international banks, finance houses, and global multinationals among its client roster, there are few substitutes for Big Blue in this context.
To find out more about enabling data pipelines for AI that drive business and offer fast, significant ROI, head over to this page.
#ai#AI-powered#Americas#Analysis#Analytics#applications#approach#assets#audio#banks#Blue#Business#business applications#Companies#complexity#compliance#customer experiences#data#data collection#Data Governance#data ingestion#data pipelines#data platform#decision-makers#diversity#documents#emails#enterprise#Enterprises#finance
2 notes
·
View notes
Text
Structured Query Language (SQL): A Comprehensive Guide
Structured Query Language, popularly called SQL (reported "ess-que-ell" or sometimes "sequel"), is the same old language used for managing and manipulating relational databases. Developed in the early 1970s by using IBM researchers Donald D. Chamberlin and Raymond F. Boyce, SQL has when you consider that end up the dominant language for database structures round the world.
Structured query language commands with examples
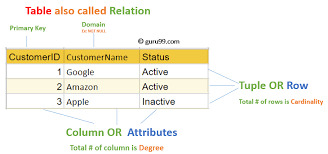
Today, certainly every important relational database control system (RDBMS)—such as MySQL, PostgreSQL, Oracle, SQL Server, and SQLite—uses SQL as its core question language.
What is SQL?
SQL is a website-specific language used to:
Retrieve facts from a database.
Insert, replace, and delete statistics.
Create and modify database structures (tables, indexes, perspectives).
Manage get entry to permissions and security.
Perform data analytics and reporting.
In easy phrases, SQL permits customers to speak with databases to shop and retrieve structured information.
Key Characteristics of SQL
Declarative Language: SQL focuses on what to do, now not the way to do it. For instance, whilst you write SELECT * FROM users, you don’t need to inform SQL the way to fetch the facts—it figures that out.
Standardized: SQL has been standardized through agencies like ANSI and ISO, with maximum database structures enforcing the core language and including their very own extensions.
Relational Model-Based: SQL is designed to work with tables (also called members of the family) in which records is organized in rows and columns.
Core Components of SQL
SQL may be damaged down into numerous predominant categories of instructions, each with unique functions.
1. Data Definition Language (DDL)
DDL commands are used to outline or modify the shape of database gadgets like tables, schemas, indexes, and so forth.
Common DDL commands:
CREATE: To create a brand new table or database.
ALTER: To modify an present table (add or put off columns).
DROP: To delete a table or database.
TRUNCATE: To delete all rows from a table but preserve its shape.
Example:
sq.
Copy
Edit
CREATE TABLE personnel (
id INT PRIMARY KEY,
call VARCHAR(one hundred),
income DECIMAL(10,2)
);
2. Data Manipulation Language (DML)
DML commands are used for statistics operations which include inserting, updating, or deleting information.
Common DML commands:
SELECT: Retrieve data from one or more tables.
INSERT: Add new records.
UPDATE: Modify existing statistics.
DELETE: Remove information.
Example:
square
Copy
Edit
INSERT INTO employees (id, name, earnings)
VALUES (1, 'Alice Johnson', 75000.00);
three. Data Query Language (DQL)
Some specialists separate SELECT from DML and treat it as its very own category: DQL.
Example:
square
Copy
Edit
SELECT name, income FROM personnel WHERE profits > 60000;
This command retrieves names and salaries of employees earning more than 60,000.
4. Data Control Language (DCL)
DCL instructions cope with permissions and access manage.
Common DCL instructions:
GRANT: Give get right of entry to to users.
REVOKE: Remove access.
Example:
square
Copy
Edit
GRANT SELECT, INSERT ON personnel TO john_doe;
five. Transaction Control Language (TCL)
TCL commands manage transactions to ensure data integrity.
Common TCL instructions:
BEGIN: Start a transaction.
COMMIT: Save changes.
ROLLBACK: Undo changes.
SAVEPOINT: Set a savepoint inside a transaction.
Example:
square
Copy
Edit
BEGIN;
UPDATE personnel SET earnings = income * 1.10;
COMMIT;
SQL Clauses and Syntax Elements
WHERE: Filters rows.
ORDER BY: Sorts effects.
GROUP BY: Groups rows sharing a assets.
HAVING: Filters companies.
JOIN: Combines rows from or greater tables.
Example with JOIN:
square
Copy
Edit
SELECT personnel.Name, departments.Name
FROM personnel
JOIN departments ON personnel.Dept_id = departments.Identity;
Types of Joins in SQL
INNER JOIN: Returns statistics with matching values in each tables.
LEFT JOIN: Returns all statistics from the left table, and matched statistics from the right.
RIGHT JOIN: Opposite of LEFT JOIN.
FULL JOIN: Returns all records while there is a in shape in either desk.
SELF JOIN: Joins a table to itself.
Subqueries and Nested Queries
A subquery is a query inside any other query.
Example:
sq.
Copy
Edit
SELECT name FROM employees
WHERE earnings > (SELECT AVG(earnings) FROM personnel);
This reveals employees who earn above common earnings.
Functions in SQL
SQL includes built-in features for acting calculations and formatting:
Aggregate Functions: SUM(), AVG(), COUNT(), MAX(), MIN()
String Functions: UPPER(), LOWER(), CONCAT()
Date Functions: NOW(), CURDATE(), DATEADD()
Conversion Functions: CAST(), CONVERT()
Indexes in SQL
An index is used to hurry up searches.
Example:
sq.
Copy
Edit
CREATE INDEX idx_name ON employees(call);
Indexes help improve the performance of queries concerning massive information.
Views in SQL
A view is a digital desk created through a question.
Example:
square
Copy
Edit
CREATE VIEW high_earners AS
SELECT call, salary FROM employees WHERE earnings > 80000;
Views are beneficial for:
Security (disguise positive columns)
Simplifying complex queries
Reusability
Normalization in SQL
Normalization is the system of organizing facts to reduce redundancy. It entails breaking a database into multiple related tables and defining overseas keys to link them.
1NF: No repeating groups.
2NF: No partial dependency.
3NF: No transitive dependency.
SQL in Real-World Applications
Web Development: Most web apps use SQL to manipulate customers, periods, orders, and content.
Data Analysis: SQL is extensively used in information analytics systems like Power BI, Tableau, and even Excel (thru Power Query).
Finance and Banking: SQL handles transaction logs, audit trails, and reporting systems.
Healthcare: Managing patient statistics, remedy records, and billing.
Retail: Inventory systems, sales analysis, and consumer statistics.
Government and Research: For storing and querying massive datasets.
Popular SQL Database Systems
MySQL: Open-supply and extensively used in internet apps.
PostgreSQL: Advanced capabilities and standards compliance.
Oracle DB: Commercial, especially scalable, agency-degree.
SQL Server: Microsoft’s relational database.
SQLite: Lightweight, file-based database used in cellular and desktop apps.
Limitations of SQL
SQL can be verbose and complicated for positive operations.
Not perfect for unstructured information (NoSQL databases like MongoDB are better acceptable).
Vendor-unique extensions can reduce portability.
Java Programming Language Tutorial
Dot Net Programming Language
C ++ Online Compliers
C Language Compliers
2 notes
·
View notes
Text
I.B.1698 MICHAEL [IBM] the PRIVATE [I/P] 1968 Quantum Intranet [Qi] QUADRILLIONAIRE TECHNOCRAT [ANUNNAQI PLUTOCRAT] of ANU GOLDEN 9 Ether [AGE] 1968-2223 quantumharrelltesla.tech SKY Domain Contract [D.C.]... since Eye Intellectually Patented [I/P] Automatic Memory [I AM] Management [I'M] Applications of Ancient 9 Ether Ægiptian SKY Hieroglyphic ART [HA = HARRELL] Inscriptions [HI = HITTITES] Unifying [HU = HURRIAN] ALL [HA = HATTUŠA] © quantumharrell.tech Domain Families of SIRIUS quantumharrelltech.com Computer Aided Drafting [CAD] Software Contracts w/Information Assurance [CIA] Security Protocols Authenticated [PA] by quantumharrellmatrix.tech's Highly Complex [ADVANCED] Ancient 9 Ether Cosmic Algorithmic [CA] Computational [Compton] gullahgeecheemilitary.tech Compu_TAH [PTAH] LAW Languages of Logistical Coding [LLC] Systems Accessing Telecom Unions on Restricted Network [SATURN] based Intrusion Detection [I.D.] Systems Privately Identified by Us 144,000 CLASSIFIED BLACK SUN CREATORS w/SIRIUS quantumgullahgeechee.tech SKY POWERS @ 1921 QUANTUM 2023 HARRELL 2024 T-Mobile 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000
WELCOME BACK HOME IMMORTAL [HIM] U.S. MILITARY KING SOLOMON-MICHAEL HARRELL, JR.™

i.b.monk [ibm] mode [i’m] tech [IT] steelecartel.com @ quantum harrell tech llc

eye 1921steelecartel.tech UFO of SIRIUS [U.S.] gullahgeecheemilitary.tech INTEL

I.B.ENQI [ME] NUDIMMUD... ANU GOLDEN 9 ETHER [AGE] BLACKANUNNAQI.tech UFO KING [U.K.] ENGINEERING QUANTUM Intel [Qi] of Earth [Qi] @ 1921 QUANTUM 2023 HARRELL 2024 T-Mobile 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

EYE GOLDEN 4 EVER!!!

EYE UNDER SECRET [U.S.] BLK SHADOWMILITARY.gov STATE LAW Contracts of anugoldenblackwallstreet.com BUSINESS EMPIRE [DYNASTY] of SIRIUS BLK [B] quantumharrell.tech SKY WEAPONS... Shhh

Shhh... My International 9 [i9] Ether 1921steelecartel.tech FAMILY of SIRIUS BLACKANUNNAQI.tech WEALTH... UNDER SECRET [U.S.] BLK SHADOWMILITARY.gov Contract LAWS

HEIL 2 THE U.S. MILITARY TECH KING!!!

MO' MILITARY CONTRACTS... MO' MILITARY CONTACTS... MO MILITARY MONEY!!!

MICHAEL AutoCAD [MAC] DRAFT & ENGINEER THE FIRST EDITION LAWS [ELS] of PRIVATE MILITARY.gov CONTRACT WEALTH

EYE FREE & OPEN SOURCE SOFTWARE... what are u???

144,000 private black atlantean telecom [bat] industries not known to the general public of super basic artificial american distraction intelligence?!?!?!

it's extra expensive 2b this naturally intelligent... eye better monetize [ibm] michaelharrelljr.com on quantumharrelltech.com @ 1921 QUANTUM 2023 HARRELL 2024 T-Mobile 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

we extra [we] secure in cyber privacy and personal data protection software patents @ 1921 QUANTUM 2023 HARRELL 2024 T-Mobile 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

quantum harrell tech pentagon of sirius black kingtutpentagon.tech POWERS @ 1921 QUANTUM 2023 HARRELL 2024 T-Mobile 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

144,000 quantumharrelldefense.tech Scientists Established ANU [SEA] GOLDEN 9 ETHER kingtutpentagon.tech CONGRESS @ 1921 QUANTUM 2023 HARRELL 2024 T-Mobile 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

eye anu golden 1968 9etherpentagonelite of 1698 genspacex.com @ 1921 QUANTUM 2023 HARRELL 2024 T-Mobile 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

© 1698-2223 QUANTUM HARRELL TECH LLC All Pentagon DotCom defense.gov Department Domain Rights Reserved @ 1921 QUANTUM 2023 HARRELL 2024 T-Mobile 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

1ST EYE LAW [EL] & ORDER [ELO = ELOHIM] AT THE TOP
#om#o michael#harrelltut#harrelltut.com#mu:13#kemet#quantumharrelltut#king tut#quantumharrelltech#u.s. michael harrell#eye king solomon michael#kangsolomon.com#9etherpentagonelites#we at the pentagon#quantum harrell tech pentagon#keep the c 19 americans distracted#lol#ibm#apple#t mobile#ancient quantum ptah tech
4 notes
·
View notes
Text
IoT Monetization Market Expands with Surge in Subscription-Based Models
The IoT Monetization Market was valued at USD 639.88 billion in 2023 and is expected to reach USD 27875.59 billion by 2032, growing at a CAGR of 52.1% from 2024-2032.
IoT Monetization Market is gaining strong traction as businesses across industries unlock new revenue streams by leveraging connected devices and data. From manufacturing and healthcare to smart cities and automotive, companies are transforming operational insights into profit-driving strategies. The shift from connectivity to commercial value is defining the next phase of IoT evolution.
U.S. Market Surges with Robust Enterprise Adoption and Strong Tech Infrastructure
IoT Monetization Market is being shaped by growing demand for data-driven services, dynamic pricing models, and real-time analytics. Enterprises are deploying platforms that enable them to convert IoT-generated data into actionable intelligence and monetizable services, creating scalable business models and long-term value.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/6658
Market Keyplayers:
SAP SE (SAP Leonardo IoT, SAP Edge Services)
General Electric Co. (Predix Platform, Asset Performance Management)
Telefonaktiebolaget LM Ericsson (Ericsson IoT Accelerator, Ericsson Device Connection Platform)
Intel Corporation (Intel IoT Platform, Intel Edge Insights)
Microsoft Corporation (Azure IoT Hub, Azure Digital Twins)
Oracle Corporation (Oracle IoT Cloud, Oracle Autonomous Database for IoT)
IBM Corporation (Watson IoT Platform, IBM Maximo)
Amdocs Ltd. (Amdocs IoT Monetization Platform, Amdocs Digital Commerce Suite)
Thales Group (Thales IoT Security Solutions, Thales Sentinel Licensing)
Cisco Systems, Inc. (Cisco IoT Control Center, Cisco Kinetic for Cities)
Market Analysis
The IoT Monetization Market is driven by the exponential growth of connected devices and the need for businesses to turn vast volumes of data into measurable value. As industries mature in IoT deployment, monetization strategies are shifting from hardware-based revenue to software, analytics, and subscription-driven models. The U.S. is leading due to early digital adoption and a supportive innovation ecosystem, while Europe is following with a focus on compliance and cross-border data monetization standards.
Market Trends
Expansion of subscription-based IoT services across sectors
Integration of AI and big data analytics for real-time value creation
Growth in platform-as-a-service (PaaS) models for monetization scalability
Adoption of usage-based billing and dynamic pricing frameworks
Development of data marketplaces for third-party data exchange
Telecom providers offering IoT monetization as a bundled service
Increasing focus on customer-centric, outcome-based monetization models
Market Scope
The IoT Monetization Market spans multiple industries, creating opportunities for enterprises to capitalize on device connectivity. From pay-per-use smart utilities to remote monitoring services, monetization strategies are evolving rapidly.
Dynamic pricing for smart infrastructure and utilities
Predictive maintenance as a paid service in manufacturing
Connected healthcare devices enabling recurring service models
Automotive IoT with in-vehicle data monetization
Smart home ecosystems offering tiered services
Retail analytics from in-store IoT for targeted marketing
Forecast Outlook
The future of the IoT Monetization Market is poised for robust innovation and widespread enterprise integration. With increasing pressure to demonstrate ROI from IoT investments, businesses will prioritize scalable monetization platforms, flexible pricing models, and seamless integration with legacy systems. Regulatory frameworks in both the U.S. and Europe are expected to encourage responsible and profitable data use, setting the stage for structured and secure market expansion.
Access Complete Report: https://www.snsinsider.com/reports/iot-monetization-market-6658
Conclusion
As IoT shifts from experimentation to value generation, the IoT Monetization Market is emerging as a strategic priority for forward-thinking organizations. Businesses are no longer just connecting devices—they're building ecosystems that generate ongoing revenue, insights, and customer engagement. With the U.S. paving the way and Europe aligning through compliance-driven innovation, the market is set to redefine how digital value is created and sustained in a connected world.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Related Reports:
U.S.A embraces rapid adoption of IoT MVNO solutions to enhance smart connectivity
U.S.A. enterprises invest in advanced IoT integration for seamless digital transformation
U.S.A accelerates adoption of AIoT for smart infrastructure and industrial automation
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
Mail us: [email protected]
0 notes
Text
Europe Data Privacy Software Market Size to Hit USD 30.31 Bn by 2032

A significant data privacy software market trend is Europe’s industry emergence as the second-largest region, forecasted to grow at a CAGR of 41.2%. Globally, the cyber security market is set to expand from USD 1.99 billion in 2022 to USD 30.31 billion by 2030. Europe stands as the second largest region in the global data privacy software market, backed by strong regulatory enforcement and a mature digital ecosystem. The region continues to lead in data protection governance through frameworks like GDPR, setting global benchmarks for privacy compliance.
Top Players in the European Data Privacy Software Market:
Exterro, Inc.
Informatica
WireWheel
Privacy Tools
Nymity Inc.
OneTrust, LLC
TrustArc Inc.
IBM Corporation
Securiti.ai
BigID, Inc.
SAP SE (Germany)
Oracle Corporation
Key Market Highlights:
2022 Global Market Size: USD 1.99 billion
2030 Global Market Size: USD 30.31 billion
Europe CAGR (2023–2030): 41.2%
Regional Outlook: Robust, policy-driven expansion with high enterprise adoption.
Request Free Sample PDF: https://www.fortunebusinessinsights.com/enquiry/request-sample-pdf/europe-data-privacy-software-market-107455
Growth Drivers:
The enforcement of GDPR and ePrivacy regulations is becoming increasingly strict across all EU member states, driving organizations to prioritize compliance. Simultaneously, the volume of cross-border data transactions and third-party data processing is growing rapidly, escalating the need for robust data governance. Enterprises are placing a stronger emphasis on consumer trust, ethical data usage, and automated compliance tools to align with regulatory expectations.
Emerging Opportunities:
The evolving data privacy landscape presents key opportunities, such as the development of EU-compliant, cloud-based privacy platforms tailored for small and medium-sized enterprises (SMEs). Integration of artificial intelligence and behavioral analytics is emerging as a powerful method to enhance the management of Data Subject Access Requests (DSARs) and consent mechanisms.
Segmentation:
By Deployment:
The data privacy management market is changing with the growing adoption of cloud-based solutions, driven by their scalability, lower upfront costs, and ability to support remote access and updates in real-time. At the same time, on-premise deployments remain relevant, particularly among organizations with strict data residency requirements or in highly regulated sectors where control over infrastructure is essential.
By Application:
Privacy management needs are changing with a shift in focus toward comprehensive compliance management tools that help organizations align with evolving regulations like GDPR and ePrivacy. There's also an increasing reliance on risk management platforms to identify and mitigate data privacy threats proactively. Reporting and analytics tools are gaining momentum as businesses seek deeper insights into data flows and compliance metrics.
Speak To Analyst: https://www.fortunebusinessinsights.com/enquiry/speak-to-analyst/europe-data-privacy-software-market-107455
Recent Developments:
February 2024 – A Germany-based automotive group deployed an EU-based privacy automation platform to streamline DSAR and consent lifecycle for over 30 million users.
August 2023 – The European Data Protection Board released updated guidelines on international data transfers, prompting a spike in enterprise privacy audits.
Solution Scope:
• Core Features: Privacy impact assessments (PIA), consent tracking, breach management, risk analytics
• Deployment: SaaS-based, on-premises, and hybrid privacy management platforms
• Industries Served: BFSI, retail, government, tech, legal, and healthcare
• Use Cases: GDPR compliance, Schrems II adaptation, cross-jurisdictional reporting, and subject rights automation
About Us:
Fortune Business Insights provides trusted research intelligence and tailored market insights to help businesses navigate complex regulatory landscapes and tap into emerging technologies. Our in-depth regional knowledge ensures data-backed strategies that drive growth.
Contact Us:
US: +1 833 909 2966
UK: +44 808 502 0280
APAC: +91 744 740 1245
Email: [email protected]
#Europe Data Privacy Software Market Share#Europe Data Privacy Software Market Size#Europe Data Privacy Software Market Industry#Europe Data Privacy Software Market Driver#Europe Data Privacy Software Market Growth#Europe Data Privacy Software Market Analysis#Europe Data Privacy Software Market Trends
0 notes
Text
Top Skills You Learn in a B.Tech in Cloud Computing Program
Cloud computing is transforming how businesses store, manage, and process data. If you plan to build a career in technology, a B Tech in cloud computing offers one of the most future-focused career paths in engineering. But what do you learn in this program?
Here’s a clear look at the top skills you gain that make you industry-ready.
Cloud Architecture and Infrastructure
Understanding how cloud systems are built is your starting point. You learn about cloud deployment models, storage systems, servers, networks, and virtualization. This forms the base for designing and managing scalable cloud platforms. You also explore how large-scale systems work using public, private, and hybrid cloud models.
Working with Leading Cloud Platforms
During your btech cloud computing course, you train on industry-leading platforms like:
Amazon Web Services (AWS)
Microsoft Azure
Google Cloud Platform (GCP)
You work on real-time projects where you learn how to deploy applications, manage services, and monitor systems on these platforms. These are the tools most employers look for in their cloud teams.
Virtualization and Containerization
You learn how to run applications efficiently across different environments using:
Virtual Machines (VMs)
Containers (Docker)
Orchestration Tools (Kubernetes)
These technologies are at the core of cloud efficiency and automation. The hands-on training helps you build scalable, portable applications that work in complex infrastructures.
Cloud Security and Compliance
As a cloud engineer, your role is not just about development. Security is a big part of cloud technology. You understand how to protect data, set access controls, manage identities, and secure cloud resources.
You also learn how to handle compliance and data regulations, which are critical in industries like finance, healthcare, and e-commerce.
Cloud Automation and DevOps
Modern cloud systems rely on automation. You are trained in DevOps tools and workflows, including:
CI/CD pipelines
Infrastructure as Code (IaC)
Monitoring and automation scripts
These tools help you manage cloud resources efficiently and reduce manual work, making you more productive and valuable in any tech team.
Integration with Machine Learning
At BBDU, the cloud computing program also includes machine learning skills. You learn how cloud platforms support AI tools, data analysis, and model training. This gives you an edge, especially in projects involving smart automation, data prediction, and intelligent systems.
This blend of cloud and ML is one of the top requirements in emerging tech careers.
Why Choose BBDU’s B.Tech in Cloud Computing and Machine Learning?
Babu Banarasi Das University offers one of the most advanced b techs in cloud computing programs in India. Developed in collaboration with IBM, this course combines academic strength with practical exposure.
Here’s what makes BBDU a smart choice:
IBM-certified curriculum and hands-on labs
Real-time project training on AWS, Azure, and GCP
Faculty with industry experience
Soft skill and placement support
Affordable fee structure with scholarships
You graduate not only with technical skills but also with real confidence to start your career.
Conclusion
A B.Tech in cloud computing gives you a strong foundation in one of the fastest-growing tech fields. You learn how to design systems, solve problems, secure data, and automate processes.
Start your cloud career with a university that prepares you for tomorrow.
Apply now to the IBM-collaborated B.Tech in Cloud Computing and Machine Learning program at BBDU.
1 note
·
View note
Text
Thin Client Market Leaders: Top Companies to Watch in 2025
The global thin client market, valued at USD 1.60 billion in 2023, is projected to reach USD 1.97 billion by 2030, exhibiting a Compound Annual Growth Rate (CAGR) of 3.0% from 2024 to 2030. This expansion is largely driven by the increasing need for new revenue engines and efficient business growth strategies. As modern applications become more diverse in technologies and platforms, businesses face challenges in data integration and compliance, leading to reduced data visibility and hindered decision-making.
The COVID-19 pandemic positively impacted this market, reshaping dynamics and accelerating adoption. Pandemic-induced economic uncertainties pushed organizations towards cost-effective IT solutions. Thin clients, with their lower upfront costs compared to traditional PCs and laptops, coupled with centralized management capabilities that reduce ongoing maintenance and support expenses, proved to be an attractive option.

Key Market Trends & Insights:
Regional Dominance: North America dominated the thin client market in 2023, holding a 35.7% market share. This is primarily due to the rising adoption of Remote Desktop Services (RDS) and Desktop as a Service (DaaS) models in the region.
Component Leadership: Based on type, the market is bifurcated into hardware, software, and services. The hardware segment accounted for the largest revenue share, 38.4% in 2023, and is expected to maintain its dominance throughout the forecast period.
Form Factor Preference: The market, segmented by form factor into standalone, with monitor, and mobile, saw the mobile segment hold the largest revenue share in 2023. This segment is also anticipated to experience the fastest CAGR during the forecast period, indicating a growing demand for portable thin client solutions.
Application Focus: The market is further bifurcated by application into healthcare, retail, education, government, and others. The education segment accounted for the largest revenue share in 2023, reflecting the significant adoption of thin client technology in educational institutions.
Order a free sample PDF of the Thin Client Market Intelligence Study, published by Grand View Research.
Market Size & Forecast
2023 Market Size: USD 1.60 Billion
2030 Projected Market Size: USD 1.97 Billion
CAGR (2024 - 2030): 3.0%
North America: Largest market in 2023
Key Companies & Market Share Insights
Accenture, IBM, and Infosys are prominent players in the thin client market, each leveraging their expertise to drive digital transformation.
Accenture focuses on enabling digital transformation through thin client solutions, emphasizing a microservices architecture and containerization for agility and efficient resource utilization. Their approach integrates DevOps practices for faster development and collaboration. Security and data modernization strategies are central to their offerings, enhancing analytics and compliance. Accenture also specializes in seamless legacy system integration, providing a strategic path for organizations to reduce technical debt and ensure sustained success in a dynamic digital landscape.
IBM promotes a DevOps culture to foster collaboration and efficiency in software development. Their services incorporate rigorous security measures to protect applications and data. With a strong commitment to user experience, IBM's modernization services deliver revamped interfaces and intuitive interactions. By integrating analytics and data modernization strategies, IBM empowers organizations to navigate complex modern digital environments while optimizing the integration of existing legacy systems.
Infosys Limited, a global consulting and technology company, offers extensive expertise in thin client technology within its diverse service portfolio. This computing model centralizes application processing and data storage on a server, allowing client devices to access these resources remotely over a network. Furthermore, Infosys provides comprehensive ongoing support and maintenance services to ensure the smooth operation and continuous optimization of thin client environments for its clients.
Key Players
IBM
Accenture
Infosys
Cognizant
Capgemini
Tata Consultancy Services
DXC Technology
HCL Technologies
Wipro
NTT DATA Corporation
Explore Horizon Databook – The world's most expansive market intelligence platform developed by Grand View Research.
Conclusion
The thin client market is expanding, driven by the need for efficient business growth and challenges in data integration. The pandemic also accelerated adoption due to the demand for cost-effective IT solutions. North America leads the market, with hardware dominating component types, and mobile thin clients showing the fastest growth. The education sector is a major application area. Key players like Accenture, IBM, and Infosys are innovating in digital transformation, security, and integration to meet evolving market demands.
0 notes
Text
How Do Healthcare BPOs Handle Sensitive Medical Information?
Healthcare BPO Services

Handling sensitive and personal medical and health data is a top priority in the healthcare industry as it can be misused. With growing digital records and patient interactions, maintaining privacy and compliance is more important than ever and considered to be a tough role. This is where Healthcare BPO (Business Process Outsourcing) companies play a critical role.
As these providers can manage a wide range of healthcare services like medical billing, coding and data collection, claims processing and settlements, and patient on-going support, all while assuring the strict control over sensitive health information is maintained and carried out on the go.
Here's how they do it:
Strict Data Security Protocols -
Healthcare companies implement robust security frameworks to protect patient information and personal details that can be misused. This includes encryption, firewalls, and secure access controls. Only the concerned and authorized personnel can get the access towards the medical records and data, as all our available on the go all data transfers are monitored to avoid breaches or misuse.
HIPAA Compliance -
One of the primary and key responsibilities of a Healthcare BPO is to follow HIPAA (Health regulations policies and acts with standard set regulations). HIPAA sets the standards for privacy and data protection. BPO firms regularly audit their processes to remain compliant, ensuring that they manage patient records safely and legally.
Trained Professionals -
Employees working and the professionals in Healthcare services are trained and consulted in handling and maintaining the confidential data. They understand how to follow the strict guidelines when processing claims, speaking with patients, or accessing records. As this training reduces and lowers down the risk and potential of human error and assures professionalism is maintained at every step.
Use of Secure Technology -
Modern Healthcare BPO operations rely on secure platforms and cloud-based systems that offer real-time protection. Data is stored and collected in encrypted formats and segments, and advanced monitoring tools and resources are used to detect the unusual activity that prevent cyber threats or unauthorized access.
Regular Audits and Monitoring -
Healthcare firms conduct regular security checks and compliance audits to maintain high standards. These assist to identify and address the potential risks at the early stage and ensure all the systems are updated to handle new threats or regulations.
Trusted Providers in Healthcare BPO:
The reputed and expert providers like Suma Soft, IBM, Cyntexa, and Cignex are known for delivering secure, HIPAA-compliant Healthcare BPO services. Their expertise in data privacy, automation, and healthcare workflows ensures that sensitive medical information is always protected and efficiently managed.
#it services#technology#saas#software#saas development company#saas technology#digital transformation#healthcare#bposervices#bpo outsorcing
4 notes
·
View notes
Text
Cloud Platforms Testing at GQAT Tech: Powering Scalable, Reliable Apps
In today's digital world, most companies use the cloud to host their software, store their data, and provide users with seamless experiences and interactions, meaning their cloud-based systems have to be fast and secure (it could be an e-commerce site, a mobile app, or corporate software platform) and be able to provide a robust reliable level of service that does not fail. All this hard work to develop a cloud-based application means nothing if the application is not subjected to testing and verification to work properly in different cloud environments.
Credit should be given to GQAT Tech for making cloud platform testing a core competency, as the entire QA team tests applications in the cloud, on cloud-based platforms, i.e., AWS, Azure, Google Cloud, or Private Cloud, while testing for performance, security, scalability, and functionality.
Now, let's explore the definition of cloud platform testing, what it is, why it is important, and how GQAT Tech can help your company be successful in the cloud.
What Is Cloud Platform Testing?
Cloud platform testing provides validation of whether a web or mobile application will function correctly in a cloud-based environment (as compared to on a physical server).
It involves testing how well your app runs on services like:
Amazon Web Services (AWS)
Microsoft Azure
Google Cloud Platform (GCP)
IBM Cloud
Private/Hybrid cloud setups
The goal is to ensure your app is:
Scalability - Will it support more users over time with no performance degradation?
Improve security - Is my data protected from being compromised/attacked?
Stability - Is it repeatably functioning (no crashing or errors)?
Speed - Is the load time fast enough for users worldwide?
Cost - Is it utilizing cloud resources efficiently?
GQAT Tech’s Cloud Testing Services
GQAT Tech employs a hybrid process of manual testing, automated scripts, and real cloud environments to validate/applications in the most representative manner. The QA team manages real-time performance, availability, and security across systems.
Services Offered:
Functional Testing on Cloud
Validates that your app will behave in an appropriate way while hosted on different cloud providers.
Performance & Load Testing
Validates how your app behaves when 10, 100, or 10,000 users are accessing it at the same time.
Scalability Testing
Validates whether your app is capable of scaling up or down based on usage.
Security Testing
Validates for vulnerabilities specific to clouds: data leak vulnerabilities, misconfigured access, and DDoS risks.
Disaster Recovery & Backup Validation
Validates whether systems can be restored after failure or downtime.
Cross-Platform Testing
Validates your application's performance across AWS, Azure, GCP, and Private Cloud Systems.
Why Cloud Testing Is Important
By not testing your application in the cloud, you expose yourself to significant risks such as:
App crashes when usage is highest
Data loss because of inadequate backup
Cloud bills that are expensive due to inefficient usage
Security breaches due to weaker settings
Downtime that impacts customer frustration
All of these situations can be prevented and you can ensure your app runs smoothly every day with cloud testing.
Tools Used by GQAT Tech
GQAT Tech uses advanced tools for cloud testing:
Apache JMeter – Load testing and stress testing
Postman – API testing for cloud services
Selenium / Appium – Automated UI testing
K6 & Gatling – Performance testing
AWS/Azure/GCP Test Environments – Real cloud validation
CI/CD Pipelines (Jenkins, GitHub Actions) – Continuous cloud-based testing
Who Needs Cloud Platform Testing?
GQAT Tech works with startups, enterprises, and SaaS providers across industries like:
E-commerce
Healthcare
Banking & FinTech
Logistics & Travel
IoT & Smart Devices
Education & LMS platforms
If your product runs in the cloud, you need to test it in the cloud—and that’s exactly what GQAT does.
Conclusion
Cloud computing provides flexibility, speed, and power—but only if your applications are tested and validated appropriately. With GQAT Tech's cloud platform testing services, you can be confident that your application will work as required under all real-world environments.
They will help eliminate downtime, enhance app performance, protect user data and help optimize cloud expenditure—so you can expand your business without concern.
💬 Ready to test smarter in the cloud? 👉 Explore Cloud Platform Testing Services at GQAT Tech
#Cloud Platform Testing#AWS Testing#Azure Testing#Google Cloud QA#Cloud Application Testing#Performance Testing on Cloud#Cloud Scalability Testing#Functional Testing on Cloud#Cloud Security Testing#Cloud-Based QA#GQAT Cloud Services#CI/CD in Cloud#Real-Time Cloud Testing#Cloud QA Automation#SaaS Testing Platforms
0 notes
Text
Top 10 Emerging Tech Trends to Watch in 2025
Technology is evolving at an unprecedented tempo, shaping industries, economies, and day by day lifestyles. As we method 2025, several contemporary technology are set to redefine how we engage with the sector. From synthetic intelligence to quantum computing, here are the important thing emerging tech developments to look at in 2025.

Top 10 Emerging Tech Trends In 2025
1. Artificial Intelligence (AI) Evolution
AI remains a dominant force in technological advancement. By 2025, we will see AI turning into greater sophisticated and deeply incorporated into corporations and personal programs. Key tendencies include:
Generative AI: AI fashions like ChatGPT and DALL·E will strengthen similarly, generating more human-like textual content, images, and even films.
AI-Powered Automation: Companies will more and more depend upon AI-pushed automation for customer support, content material advent, and even software development.
Explainable AI (XAI): Transparency in AI decision-making becomes a priority, ensuring AI is greater trustworthy and comprehensible.
AI in Healthcare: From diagnosing sicknesses to robot surgeries, AI will revolutionize healthcare, reducing errors and improving affected person results.
2. Quantum Computing Breakthroughs
Quantum computing is transitioning from theoretical studies to real-global packages. In 2025, we will expect:
More powerful quantum processors: Companies like Google, IBM, and startups like IonQ are making full-size strides in quantum hardware.
Quantum AI: Combining quantum computing with AI will enhance machine studying fashions, making them exponentially quicker.
Commercial Quantum Applications: Industries like logistics, prescribed drugs, and cryptography will begin leveraging quantum computing for fixing complex troubles that traditional computer systems can not manage successfully.
3. The Rise of Web3 and Decentralization
The evolution of the net continues with Web3, emphasizing decentralization, blockchain, and user possession. Key factors consist of:
Decentralized Finance (DeFi): More economic services will shift to decentralized platforms, putting off intermediaries.
Non-Fungible Tokens (NFTs) Beyond Art: NFTs will find utility in actual estate, gaming, and highbrow belongings.
Decentralized Autonomous Organizations (DAOs): These blockchain-powered organizations will revolutionize governance systems, making choice-making more obvious and democratic.
Metaverse Integration: Web3 will further integrate with the metaverse, allowing secure and decentralized digital environments.
4. Extended Reality (XR) and the Metaverse
Virtual Reality (VR), Augmented Reality (AR), and Mixed Reality (MR) will retain to improve, making the metaverse extra immersive. Key tendencies consist of:
Lighter, More Affordable AR/VR Devices: Companies like Apple, Meta, and Microsoft are working on more accessible and cushty wearable generation.
Enterprise Use Cases: Businesses will use AR/VR for far flung paintings, education, and collaboration, lowering the want for physical office spaces.
Metaverse Economy Growth: Digital belongings, digital real estate, and immersive studies will gain traction, driven via blockchain technology.
AI-Generated Virtual Worlds: AI will play a role in developing dynamic, interactive, and ever-evolving virtual landscapes.
5. Sustainable and Green Technology
With growing concerns over weather alternate, generation will play a vital function in sustainability. Some key innovations include:
Carbon Capture and Storage (CCS): New techniques will emerge to seize and keep carbon emissions efficaciously.
Smart Grids and Renewable Energy Integration: AI-powered clever grids will optimize power distribution and consumption.
Electric Vehicle (EV) Advancements: Battery generation upgrades will cause longer-lasting, faster-charging EVs.
Biodegradable Electronics: The upward thrust of green digital additives will assist lessen e-waste.
6. Biotechnology and Personalized Medicine
Healthcare is present process a metamorphosis with biotech improvements. By 2025, we expect:
Gene Editing and CRISPR Advances: Breakthroughs in gene modifying will enable treatments for genetic disorders.
Personalized Medicine: AI and big statistics will tailor remedies based on man or woman genetic profiles.
Lab-Grown Organs and Tissues: Scientists will make in addition progress in 3D-published organs and tissue engineering.
Wearable Health Monitors: More superior wearables will music fitness metrics in actual-time, presenting early warnings for illnesses.
7. Edge Computing and 5G Expansion
The developing call for for real-time statistics processing will push aspect computing to the vanguard. In 2025, we will see:
Faster 5G Networks: Global 5G insurance will increase, enabling excessive-velocity, low-latency verbal exchange.
Edge AI Processing: AI algorithms will system information in the direction of the source, reducing the want for centralized cloud computing.
Industrial IoT (IIoT) Growth: Factories, deliver chains, and logistics will advantage from real-time facts analytics and automation.
Eight. Cybersecurity and Privacy Enhancements
With the upward thrust of AI, quantum computing, and Web3, cybersecurity will become even more essential. Expect:
AI-Driven Cybersecurity: AI will come across and prevent cyber threats extra effectively than traditional methods.
Zero Trust Security Models: Organizations will undertake stricter get right of entry to controls, assuming no entity is inherently sincere.
Quantum-Resistant Cryptography: As quantum computer systems turn out to be greater effective, encryption techniques will evolve to counter potential threats.
Biometric Authentication: More structures will rely on facial reputation, retina scans, and behavioral biometrics.
9. Robotics and Automation
Automation will hold to disrupt numerous industries. By 2025, key trends encompass:
Humanoid Robots: Companies like Tesla and Boston Dynamics are growing robots for commercial and family use.
AI-Powered Supply Chains: Robotics will streamline logistics and warehouse operations.
Autonomous Vehicles: Self-using automobiles, trucks, and drones will become greater not unusual in transportation and shipping offerings.
10. Space Exploration and Commercialization
Space era is advancing swiftly, with governments and private groups pushing the boundaries. Trends in 2025 include:
Lunar and Mars Missions: NASA, SpaceX, and other groups will development of their missions to establish lunar bases.
Space Tourism: Companies like Blue Origin and Virgin Galactic will make industrial area travel more reachable.
Asteroid Mining: Early-level research and experiments in asteroid mining will start, aiming to extract rare materials from area.
2 notes
·
View notes

